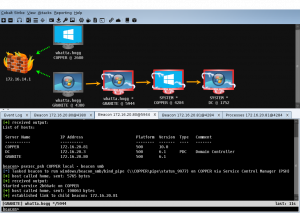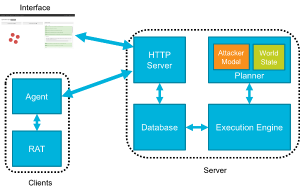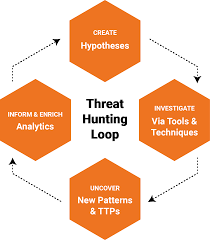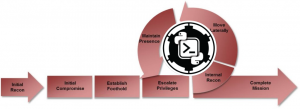
In this blog post, I continue my pursuit of knowledge to become a threat hunter. This blog post will introduce the following concepts: understanding the attacker mindset with the Mandiant Attack Lifecycle, performing a red team exercise to demonstrate the tools and techniques used by attackers with Powershell Empire, and observing how attacker activity leaves behind a trail of artifacts. These concepts will create the foundation we will use in future blog posts to hunt for malicious activity.