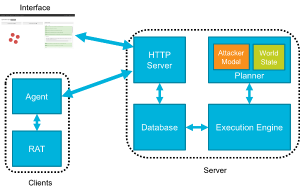
In this blog post I will be covering how to setup and utilize MITRE’s new tool called Caldera. Caldera is a cyber adversary emulation system that operates on a server/agent model. On the server you can create adversary campaigns that are deployed to your agents. Your agents will periodically call back with their results and progress. Let’s begin!
Install/Setup Caldera on Ubuntu 16.04
Deploy Caldera with Ansible – prod
- git clone https://github.com/Benster900/BlogProjects.git
- cd BlogProjects/CalderaMitre
- vim hosts and set [caldera]
- mv group_vars/all.example group_vars/all
- vim group_vars/all and set:
- base_domain
- caldera_pass
- cert info
- ansible-playbook -i hosts deploy_caldera.yml -u
- Browse to “https://<IP addr of Caldera server>” and login
- user: admin
- pass: {{ caldera_pass }}
Deploy Caldera with Docker – dev
- git clone https://github.com/Benster900/BlogProjects.git
- cd BlogProjects/CalderaMitre
- docker build -t caldera .
- docker run -d -p 8888:8888 –hostname=<FQDN> caldera
- A DNS entry MUST be made to point at the host running the Docker container. Caldera uses the hostname of the Docker container which is only accessible within the Docker network but “–hostname” flag corrects that.
- MongoDB is built into the docker container so this means the data will NOT persist.
- Browse to “https://127.0.0.1:8888” and login
- user: admin
- pass: caldera
Deploy Caldera agents to Windows clients
- vim hosts and set [win_agents]
- mv group_vars/windows.example group_vars/windows
- vim group_vars/windows and set:
- ansible_user: <Windows username>
- ansible_password: <Windows user password>
- ansible-playbook -i hosts deploy_windows_agents.yml
- Browse to “https://127.0.0.1:8888” and login
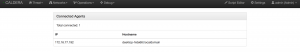
- Select “Debug” then “Connected agents”
Becoming the hunter
Creating an adversary
To perform an Operation, CALDERA needs an Adversary to emulate. In CALDERA, an Adversary represents a real adversary’s tactics and techniques. When we create our operation we will select an Adversary to use which will dictate what techniques CALDERA performs during the operation.
- Select “Threat” then “Create adversary”
- Enter “test_adversary” as the name
- Select different adversary tactics from the steps drop down menu
- get_computers
- get_domain
- get_local_profiles
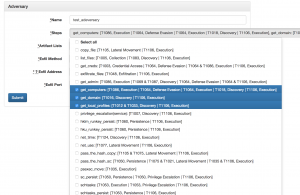
- Select “http” for exfil method
- Leave exfil address as default
- Enter “8889” for exfil port
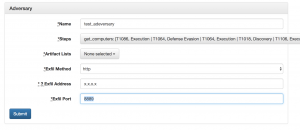
- Select “Submit”
Creating a network
Networks are just collections of host. They are a simple way for CALDERA to organize and group together computers.
- Select “Networks” then “Create network”
- Enter “test_network” for name
- If you connected to a domain select the domain but this computer is NOT part of a domain
- Select the hosts you want to participate in the simulation
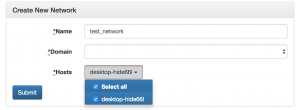
- Select “Submit”
Creating an operation
- Select “Operations” then “Create operation”
- Enter “test_op” for name
- Select “test_adversay” for adversary
- Select “test_network” for network
- Select a starting host
- I only have one host for this demo
- Select “bootstrap rat” for start method
- Leave start path blank
- Select “active user” as the starting user
- Enter “explorer.exe” for parent process
- UNcheck “Auto-cleanup”
- I want to leave the artifacts behind for future posts 🙂
- Enter a desired command delay
- Enter a desired jitter
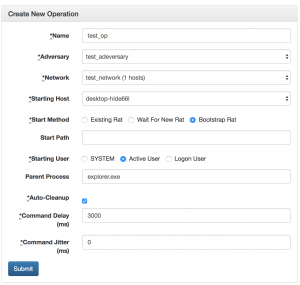
- Select “Submit”
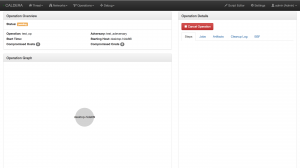
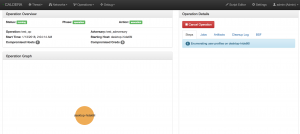
Watch operation
In the Operation view, you can view the progress that CALDERA has made working on an operation. The operation’s status is displayed at the top of the screen next to the Operation’s name. Below the status, colored bubbles indicate the number of hosts and credentials that have been compromised during this operation.
Where to go from here?
MITRE has created a really awesome tool here for defenders. This tool can help you evaluate your security team’s effectiveness at detecting different red team tactics. Cyb3rWard0g provides a scoring system for tactics outlined in the MITRE ATT&CK framework. His scoring system starts at none(no detection) too excellent(automated detection).
In the coming months, I will be taking advantage of Cyb3rWardog’s scale and this tool for my threat hunting and incident response projects. A majority of my projects require an adversary and I want to quantify my progress at detecting various techniques. As my projects and skills progress, this tool provides the capability to reproduce an attack to accurately measure my effectiveness. Additionally, this tool provides the ability to extend the adversarial tactics and capabilities. Personally, I think it would be awesome to combine the Powershell Empire API and this tool :).
Are you running the Ubuntu host in a virtual machine or on hardware? I can’t seem to get any hosts to connect to the containerized deploy under a virtual machine. I see a connection from my Windows hosts over 8888, but they never show in the connection list.
Try running “docker run -d -p 8888:8888 –hostname=[FQDN] caldera”. A DNS entry MUST be made to point at the host running the Docker container. By default, Caldera uses the hostname of the Docker container which is only accessible by the docker network but the ‘–hostname’ flag corrects that. The README will be updated shortly. Thanks!
Hello, I tried to run both the installation and docker image but get the same error…
Traceback (most recent call last):
File “caldera.py”, line 16, in
from app import server
File “/opt/caldera/caldera/app/server.py”, line 13, in
from aiohttp import web, WSCloseCode
File “/usr/local/lib/python3.5/dist-packages/aiohttp/web.py”, line 15, in
from . import (hdrs, web_exceptions, web_fileresponse, web_middlewares,
File “/usr/local/lib/python3.5/dist-packages/aiohttp/web_middlewares.py”, line 5, in
from aiohttp.web_urldispatcher import SystemRoute
File “/usr/local/lib/python3.5/dist-packages/aiohttp/web_urldispatcher.py”, line 20, in
from yarl import URL, unquote
ImportError: cannot import name ‘unquote’
Any Recommendations on how to get past this?
Hey Kyle,
I just commented on your Github ticket but it seems YARL has removed unquote from the lastest commit
Drop yarl.quote and yarl.unquote public functions (#155)
Source: https://github.com/aio-libs/yarl/blob/829f6568916f9f3219a940720bee65103ca591c2/CHANGES.rst
Hey Kyle,
It seems to be aiohttp==2.3.2 needs to be aiohttp==2.3.8 in the requirements.txt. My code has a sed statement to correct this.
why the status is always pending?
Hey JustPlay,
On your Windows host install Wireshark, start a Wireshark capture, and then start the CALDERA agent. Verify that the agent is calling back to the right port(8888 by default) and to the correct IP address. Next, verify the CALDERA config for the agent is correct, config can be viewed by browsing to https://:8888/conf.yml. Lastly, I would look at the CALDERA documentation to setup an agent.