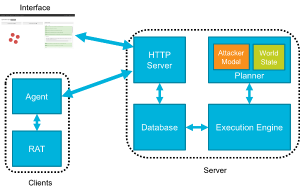
This blog post series is for anyone who has ever had an interest in threat hunting but did not have the knowledge of how or where to start, what tools they need, or what to hunt for. In this blog post, I will introduce an informal threat hunting process by hunting the APT-style attack performed during the red team exercise in the previous blog post. The theme of this blog post is to demonstrate how to hunt and detect malicious activity at each stage of the Mandiant Attack Lifecycle to create a fundamental framework for hunting adversaries. This blog post is a written adaptation of my DefCon 2020 Blue Team village workshop. It will utilize the same ideas and techniques used for that workshop reiterating specifics and points for the greater InfoSec community to use.