I have to be honest that my red team skills could use some improvement. I firmly believe that red teaming is a skill and a mindset that people have. I believe some people are naturally born with this mindset and others develop it, I am a developer :).Currently, I am aspiring to become an incident responder because the thrill of the hunt seems like A LOT of fun to me. But to be an effective incident responder I have to understand my adversary and their strategies.
This blog post series will include my approach of learning how to become a red teamer in a competition type of environment. Now my reasoning for this is because I have the ability to compete in multiple competitions as red teamer as a college student. Additionally, I hope to periodically return to these posts and update them with new tactics and tools that I find and use.
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
DISCLAIMER
Breaking down the competition methodology
Red vs. blue competitions are a means to give blue teams a sense of what it is like to be attacked. It is the job of the red team to emulate threat actors that blue team members may encounter in the real world. Red team also has the role and responsibility to challenge blue teams based on their skills but also teach them. This is one of the biggest gaps in all competitions is the transfer of knowledge from red team to blue team. Being a blue teamer for four I have always been thankful for the red team engagements I was apart of and the dedication of the red teamers. But I feel blue teamers never get the amount of time or attention they need from red team members to improve. I hope my blog posts starts a discussions with people starting in security and looking to improve their skills.
Scanning and enumeration
At RIT I had the privilege to be an e-board member of a club called RC3(rc3.club). Every Fall we would get a new round of freshmen and almost 90% of the freshmen aspired to do pen testing. Without a doubt almost every freshmen wanted to jump straight into exploiting boxes without understand the basics, understanding the exploits, and most importantly didn’t understand their environment.
Scanning and enumeration allows a red teamer to understand their environment. These scans give a base jump point for red teamers to leverage vulnerabilities in the various systems.Scanning is finding all available TCP and UDP network services running on the targeted hosts. This can help a red teamer discover if SSH is open to try a brute force login, discover file storage shares to download data from, or websites that may have vulnerabilities. Enumeration is discovery of services on the network to obtain a greater sense of information provided by the network services. This post will cover the various techniques and methods for scanning and enumeration on a system.
Scanning
ARP scanning
This method takes advantage of how ARP works by sending ARP broadcast. Each ARP broadcast frame requests who has an IP address that is increased by one each time. If a host has that IP address it will respond to the request with the requested IP address and the it’s MAC address. ARP scanning is effective, fast, and typically won’t set off any alarms. However, the issue with ARP is it’s a layer 2 protocol so it can’t go over network boundaries. Meaning if red team is on network 10.100.0.0/24 and a blue team is on network 172.16.X.0/24 then you can’t send ARP requests to 172.16.X.0/24. There are numerous tools to do this but the most popular is “arp-scan”.
arp-scan tool
- arp-scan –interface=eth0 –localnet
- –interface: tells arp-scan which interface to use to send arp requests
- –localnet: Generates the network ID and netmask from the interface specified above
ARP Broadcast request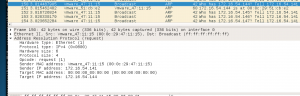
ARP Broadcast reply
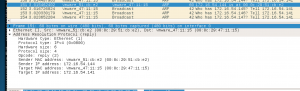
The network mapper(NMAP)
NMAP is the most popular tool used for port scanning and enumeration. I will not cover all the NMAP options and modules in this guide because that in itself is a series. I will cover the scans that I use the most when red teaming.
Port states
- Open – Open means that an application on the target machine is listening for connections/packets on that port.
- Closed -Closed ports have no application listening on them, though they could open up at any time.
- Filtered – Filtered means that a firewall, filter, or other network obstacle is blocking the port so that Nmap cannot tell whether it is open or closed.
NMAP options
- -O: OS detection
- -p: Port scan
- -p-: Scan all ports (1-65535)
- -p 80,443: Scan port 80 and 443
- -p 22-1024: Scan ports 22 through 1024
- –top-ports X: X is a number and it will scan X number of top popular ports. I usually use 100 for a quick scan which
- -sV: Service Detection
- -Tx: Set scan speed
- -T1: Really slow port scan
- -T5: Really fast port scan(really noisy)
- -sS: Stealth scan
- -sU: UDP scan
- -A: OS detection, version detection, script scanning, and traceroute
NMAP port scanner TCP scan
This option will start by initiating(SYN) a connection on each port on a target host. If the port is open the host will answer the request(SYN, ACK). The connection is closed with a reset(RST) sent by the initiator.
NMAP half-open/stealth scan
This option will start by initiating(SYN) a connection on each port on a target host. If the port is open the host will answer the request(SYN, ACK).If the port is closed the host will answer with request with a connection reset(RST). If no response is received it is assumed that the port is filtered. The difference between TCP scan and a stealth scan is the connection initiator will not respond with an acknowledgement(ACK). Now this is an effective scan because since a full connection wasn’t established it won’t be logged.
NMAP OS detection
This option will use various techniques at the operating system level to identify the operating system. The operating system type and version is very useful for vulnerability detection. Doing a quick search on OS version will show know vulnerabilities and exploits for the operating system.
- nmap 172.16.54.144 -O
NMAP service detection
This option will use various techniques to identify a specific service and it’s version running on a port. The service type and version is very useful for vulnerability detection. Doing a quick search on the service version will show know vulnerabilities and exploits for the network service.
- nmap 172.16.54.144 -sV
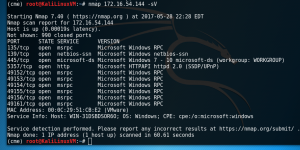
NMAP ping sweeps
This option will send an ICMP request to every IP address in a given range. If the host is alive AND responding to ping requests it will reply with an ICMP reply.
- nmap 172.16.54.0/24 -sP
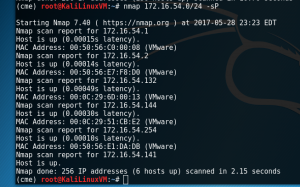
My method
Typically, in a red team engagement the red team knows the IP scheme and network services of the team(s) they are attacking. As a competition organizer we want our red team to be successful but not obliterate our blue teams. We want our red teamers to get and gain persistence and give them enough guidance to do their job. I typically start with network scan of all hosts and scan the top 100 ports on each. Second, I start an intensive scan that will scan all hosts on a network, scan all ports on each machine, and service version identification for vulnerability detection.
- nmap –top-ports 100 -T5 172.16.X.0/24
- nmap -p- -sV 172.16.X.0/24
Enumeration
SMB shares
This technique has several benefits which are
DNZ Zone transfer
DNS is my FAVORITE protocol because it’s a treasurer trove of information. Just about everyone uses DNS because who wants to remember IP addresses?!?! Being able to request a zone transfer allows an attacker to get all the DNS records for a particular zone. These records identify the hostname to IP address relationship of all hosts on your network. If the attacker have prior knowledge of the network scheme this is the fastest method to discover all hosts on a network. DNS can also contain services that are running on the network such as mail servers.
DNSrecon
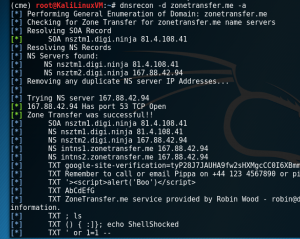
DNSrecon is the go to tool for DNS recon and enumeration. For this example we are going to request a zone transfer from zonetransfer.me. The DNS server at zonetransfer.me will return all the records it is aware of for zonetransfer.me and all subdomains. The zone transfer below tells us the nameservers with there respective hostnames and IP addresses for the domain. Returned all DNS records which were TXT records(4), PTR record(1), MX records for mail servers(10), IPv6 A record(2), 12 IPv4 A records. Now the A records provide some really juicy information about the network. One A record shows IP address of their DC office, another shows the IP address of their firewall appliance, another shows they have a VPN and it’s IP address, another A record shows the IP address of the mail server login portal.
- dnsrecon -d zonetranfer.zone -a
- -d: domain
- -a: perform zone transfer
SNMP devices
Simple Network Management Protocol(SNMP) is used to log and manage network devices and applications. SNMP can be used to configure devices and applications remotely if left insecure. SNMP can also be used to pull down information about application and devices. This information can be used to understand the network in more depth.
snmpwalk
snmpwalk is the only tool I could fine for SNMP.
- snmpwalk 172.16.1.1 -c PUBLIC
- -c: Community string to authenticate to device
Packet captures
Packet capturing packets between two hosts can be very helpful when diagnosing networking issues or credential sniffing.
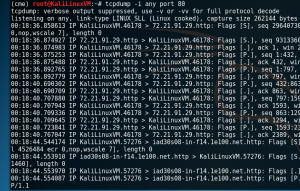
TCPdump
Command line utility used to sniff particular types of traffic and data off the wire.
- -i eth0: Select interface to liste on
- port 80: Select port to listen on
- host 172.16.1.1: Only collect traffic going to/from host
- src: Data coming from
- dst:Data going to
- -w output.pcap: Capture traffic to file on disk
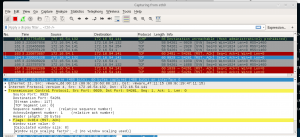
Wireshark
GUI utility used to sniff traffic off the wire.
- ip.addr/ip.dst/ip.src == 172.16.1.1
- tcp.port/tcp.dstport/tcp.srcport == 80
- udp.port/udp.dstport/udp.srcport == 53
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
The article offers a great introduction to red teaming, focusing on scanning and enumeration as the foundational steps. It emphasizes how these techniques help in identifying vulnerabilities within a network, which is crucial for preparing and defending against potential cyberattacks. The step-by-step approach provides valuable insight into practical tools and methods used in ethical hacking.