
In this blog post series, I will be covering how to setup a Tor exit node for security research. The educational goals of this series is to learn more about network security monitoring, logging, and enrichment to create a threat intelligence pipeline. My exit node will collect data that will be ingested and returned to the community as intelligence.
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
DISCLAIMER
UPDATE
Date: 3-27-18
Bandwidth monitor section
UPDATE
Why run a Tor exit node?
I have two reasons for running a Tor exit node: to give back to the community and for security research. I believe in the TOR project because it allows users to access to the Internet with NO RESTRICTIONS. Every day you read a news article about some country creating some new law to reduce privacy of users or restrict users. TOR provides a mechanism for these users to access the internet anonymously.
Secondly, just like anything TOR can be used for good and for bad. I hope to learn more about network security monitoring by implementing controls to detect and/or prevent malicious activity. My long term plan is to share my threat intelligence with the security community. For this project, I will be setting up BRO network security monitor, OSquery for host logging, and Rsyslog for shipping logs.
Within my home lab, I will implement a threat intelligence pipeline. This pipeline will ingest logs from my TOR node via Rsyslog. Next, these logs will be ingested by a data processor that will enrich the log data with data from VirusTotal. If VirusTotal reports that indicator being malicious, a Slack notification will be generated. Finally, this data will be ingested by Splunk.
The good and the bad
- Running a Tor Exit Node for fun and e-mails
- Tips for Running an Exit Node
- Five Years as an Exit Node Operator
- Running Powerful Tor Exit nodes and What I Learned Along the Way
- A Torifying Tale: Our experiences building and running Tor servers
- Thoughts on Running a Tor Exit Node for a Year
- LeaseWeb disconnects Tor exit node for forum “spam”
- Searching for “good” ISPs
Why Leaseweb?
I spent DAYS clicking on every blog post about running TOR exit nodes and looking into “know good VPS providers” by TOR. It was really hard to find a VPS that allowed TOR exit nodes that is within a country with good privacy laws and for a reasonable price. LeaseWeb is on the TOR list of VPSs that allow TOR exit nodes and it’s located in the Netherlands – which has good privacy laws, and the best pricing for the resources I wanted.
- “Although its located in the Netherlands, Germans could try Leaseweb. They’re hosting more than one *big* Tor-server and are quite tolerant.”
- “John Brooks runs a 2TB node at LeaseWeb. He would recommend them for running a relay. — JensKubieziel. In a mail to Tor-talk, a LeaseWeb employee (Alex de Joode) offered his help to sort out complaints regarding Tor.”
Create e-mail account
Before we begin, it is a good idea to create a Google Gmail or Proton mail account for Tor abuse complaints. I personally, created my own Proton e-mail account for this project.
Leaseweb VPS
Purchase instance
- Browse to https://www.leaseweb.com
- Select “Products” then “Virtual servers” under “Cloud”
- Instance type
- I selected the “Medium(M)” type of instance

- I selected the “Medium(M)” type of instance
- Size and Data center
- I selected “Amsterdam”
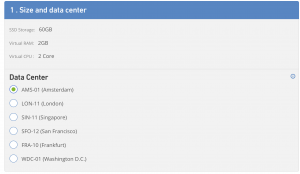
- I selected “Amsterdam”
- Software
- I selected None for backups
- I selected “Ubuntu 18.04” for OS
- I Selected None for cPanel
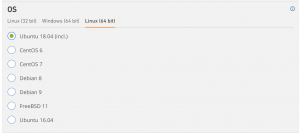
- Network
- Accepted defaults
- Contract
- Accepted defaults
- Continue to checkout
Creating account
- You will receive an e-mail within 24 hour on how to create your account
- Follow the steps within the e-mail
Enable 2FA
- Select “<your name>” in the top right and select “My profile” from the drop down menu
- Select “Two-factor authentication”
- Select your preferred method
- I choose “App” to use Google Authenticator
- Select “I trust this device” to complete the 2FA setup
Create a ticket with Leaseweb about the Tor node
My initial e-mail
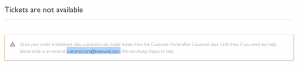
LeaseWeb does not have any issues with users running TOR exit nodes. However, it is a good idea to let them know you are running an exit node. Unfortunately, you are restricted from creating tickets within the first 48 hours, as shown above. I created an e-mail to [email protected] stating the following:
[Shell]
Subject: <Full name> – <LeaseWeb order number> – TOR exit node
Hey LeaseWeb,
I would like to inform you that I am running a Tor exit node on<IP addr of VPS>. My default TOR exit policy, rejects SMTP traffic on port 25 to block spam and blocks common BitTorrent ports. The TOR exit node is publicly displaying <TOR abuse e-mail> for abuse complaints but you can reach me on the account e-mail I registered with. Thanks.
[/Shell]
LeaseWeb’s e-mail response
Enable your instance
- Go back to the main menu
- Select “Virtual server”
- Select the play button for your instance
Setup firewall
- Select “Manage” for your instance
- Select the “Firewall” tab
- Select “Turn On” to enable the firewall
- Allow SSH
- Select “TCP” for protocol
- Enter “0.0.0.0/0” for wildcard
- Enter “22” for start port
- Enter “22” for end port
- Enter “Allow SSH” for name
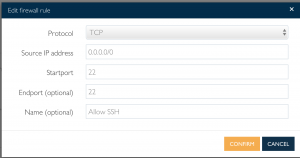
- Select “Confirm”
- Allow PING with ICMP
- Select “ICMP” for protocol
- Enter “0.0.0.0/0” for wildcard
- Enter “Allow ping requests” for name
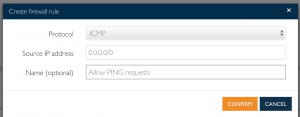
- Select “Confirm”
- Allow TOR on port 9001
- Select “TCP” for protocol
- Enter “0.0.0.0/0” for wildcard
- Enter “9001” for start port
- Enter “9001” for end port
- Enter “Allow TOR” for name
- Select “Confirm”
- Allow tor web info paage and theonionbox on port 80
- Select “TCP” for protocol
- Enter “0.0.0.0/0” for wildcard
- Enter “80” for start port
- Enter “80” for end port
- Enter “Allow TOR” for name
- Select “Confirm”
- Allowtor web info paage and theonionbox on port 443
- Select “TCP” for protocol
- Enter “0.0.0.0/0” for wildcard
- Enter “443” for start port
- Enter “443” for end port
- Enter “Allow TOR” for name
- Select “Confirm”Select “Create rule”
- Allow SSH
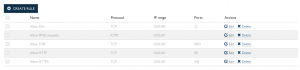
Enable bandwidth monitor
- Select “Manage” for your instance
- Select the “Data traffic notifications” tab
- Enter an e-mail for “Send to emails”
- Enter the amount of bandwidth you purchased into the “Limit” field
- Mine is 13 TB
- Set Frequency to “Daily”
- Set “Actions” to ON
- This will TURN OFF your instance when the threshold above it met
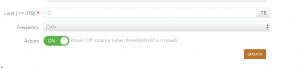
- This will TURN OFF your instance when the threshold above it met
- Select “Update”
Initial setup of instance
Get root password
- Select the “Sever information” tab
- Select “Show” next to password
- Copy this password
Create sudo user
ssh-copy-id root@<IP addr of VPS>- Enter password from above
ssh root@<IP addr of VPS>passwd root- Change root password
adduser <username>- Enter password
- Enter user info
usermod -aG sudo <username>exit
Setup/Configure SSH
ssh-copy-id <new user>@<IP addr of VPS>ssh <new user>@<IP addr of VPS>sed -i 's/PermitRootLogin yes/PermitRootLogin no/g' /etc/ssh/sshd_config- Disable root login
sed -i 's/PasswordAuthentication yes/PasswordAuthentication no/g' /etc/ssh/sshd_config- Disable password login
sed -i 's/AllowTcpForwarding yes/AllowTcpForwarding no/g' /etc/ssh/sshd_config- Disable TCP forwarding
sed -i 's/X11Forwarding yes/X11Forwarding no/g' /etc/ssh/sshd_config- Disable X11 forwarding
systemctl restart ssh
Manual software upgrade
apt-get update -y && apt-get upgrade -y- Takes roughly 20mins
apt-get autoremove -yreboot
Configure Cloudflare
This section is not required but I can never remember my IP addr for my VPS. Additionally, the Ansible setup relies on a FQDN for web applications provided by NGINX.
- Browse to “https://www.cloudflare.com” and login
- Select your domain
- Create an A record
- Enter “tor” for name
- Enter “<IP addr for VPS>” into address
- Set the TTL to “5 mins”
- DEselect the cloud

- Select “Add record”
Install/Setup TOR exit node
TOR Exit node policy
The TOR exit node policy acts as a “firewall” for what type of traffic your exit node will accept and forward. By default the policy included in my GitHub repo blocks all SMTP traffic on port 25 for spam and rejects the common port range for BitTorrent. This setup is the same policy provided by TOR, here.
Deploy TOR exit node
git clone https://github.com/CptOfEvilMinions/FireMillTor.git- vim conf/tor/torrc
- If you would like to modify the default policy
- vim group_vars/all.yml and set:
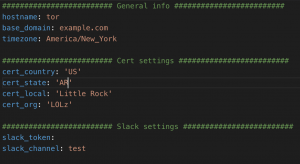
- hostname – Hostname of the box from above
- base_domain – Set domain the domain from above
- timezone – Timezone of your choosing – By default set to New York
- Cert info – Cert info for generation
- slack_token and slack_channel – Optional but this will send you Slack notifications during the Ansible setup
- vim group_vars/tor.yml and set:
- tor_nickname – Nickname for your tor exit node
- tor_abuse_email – E-mail to be contacted at for abuse
-
tor_relay_bandwidth_rate – Maximum bandwidth that Tor can use
-
tor_relay_bandwidth_burst – Burst for when the node hits the maximum rate
- vim group_vars/theonionbox.yml and set:
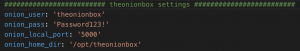
- onion_user – By default is set to theonionbox
- onion_pass – Set password
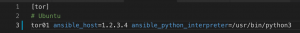
- vim hosts.ini and set:
-
ansible_host – Set to IP/FQDN of your VPS
-
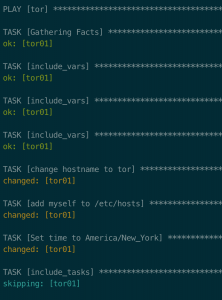
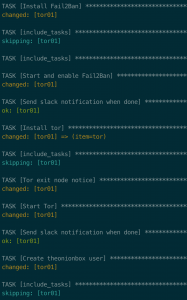
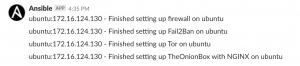
ansible-playbook -i hosts.ini deploy_tor_exit_node.yml -u <user> -K- Enter password for user
Tor web notice
- Browse to “http[s]://<IP addr of VPS>

This web page is displayed via HTTP and HTTPS. Anyone who travels to your node will be greeted with this page, which is helpful in the case of abuse from your TOR exit node. This webpage explains to them what TOR is, why attacks are coming from your VPS instance, and how to contact you.
Access theonionbox
- Browse to “https://<IP addr of VPS>/theonionbox
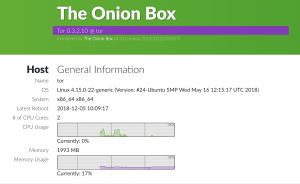
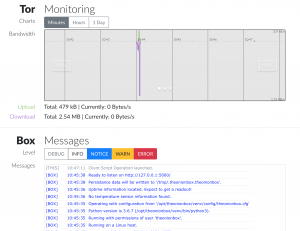
Final note
To anyone running a TOR node(exit or not) or thinking about.
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.