
While working on my TOR relay project I was trying to compile Suricata with pf_ring but couldn’t find any documentation for the latest releases. This blog post will provide instructions to compile the latest stable version of Suricata and pf_ring. In addition, this blog post contains instructions for the infrastructure-as-code written in Ansible to automate the installation and step-by-step instructions for a manual installation.
Background
What is PF_RING?
PF_RING is a high speed packet capture library that turns a commodity PC into an efficient and cheap network measurement box suitable for both packet and active traffic analysis and manipulation.
What is Suricata
Suricata is an open source network threat detection engine that provides capabilities including intrusion detection (IDS), intrusion prevention (IPS) and network security monitoring. It does extremely well with deep packet inspection and pattern matching which makes it incredibly useful for threat and attack detection.
Automate compiling Suricata and PF_RING with Ansible
git clone https://github.com/CptOfEvilMinions/BlogProjects.gitcd BlogProjects/suricatav5-pf_ringvim hosts.ini- Replace
172.16.125.130with the IP address of the host to run this playbook on - Save and exit
- Replace
vim groups_vars/all.yml- Replace
ens33formonitoring_interfacewith the interface you want Suricata to monitor - Save and exit
- Replace
ansible-playbook -i hosts.ini deploy_suricata_pf_ring.yml -u <user with admin perms> -K- Enter a password for user
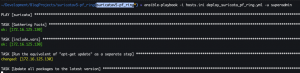
- Enter a password for user
Manually compile Suricata and PF_RING
Update kernel and freeze it
apt update -y && apt upgrade -y && apt dist-upgrade -y && apt autoremove -y- Update system and kernel
- Install Linux kernel headers
- REBOOT
apt install linux-headers-$(uname -r)apt --purge autoremoveapt-mark hold linux-image-generic linux-headers-generic- DISABLING kernel updates
- Because we compiled PFRing in this kernel, any kernel builds may cause the PFRing module to fail to load. You will need to recompile PFRing if you update your kernel after compiling.
Compile and install PF_RING v7.6.0
apt install wget cmake make gcc g++ flex git bison libpcap-dev libssl-dev python3-dev swig zlib1g-dev libgeoip-dev build-essential libelf-dev pkg-config -y- Install dependencies
cd /tmp && wget https://github.com/ntop/PF_RING/archive/7.6.0.tar.gz- Download PF_RING
tar -xvzf 7.6.0.tar.gzmv PF_RING-7.6.0 /opt/pf_ring && rm /tmp/7.6.0.tar.gz- Kernel module
cd /opt/pf_ring/kernelmake- Make pf_ring kernel module
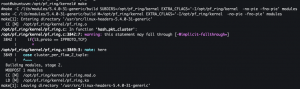
- Make pf_ring kernel module
make install- Install kernel module
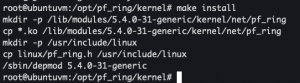
- Install kernel module
insmod ./pf_ring.ko- Load kernel module
- Libpf_ring
cd ../userland/lib./configuremakemake install
- Libpcap
cd ../../userland/libpcap./configuremakemake install
cp /opt/pf_ring/package/usr/local/bin/pf_ringctl /usr/local/bin/pf_ringctl- Copy
pf_ringctlto an executable path
- Copy
cp /opt/pf_ring/package/etc/systemd/system/pf_ring.service /etc/systemd/system/pf_ring.servicesystemctl daemon-reloadsystemctl enable pf_ringsystemctl start pf_ringsystemctl status pf_ring
Compile and install Suricata v5.0.3
apt install libpcre3 libpcre3-dbg libpcre3-dev build-essential libpcap-dev libnet1-dev libyaml-0-2 libyaml-dev pkg-config zlib1g zlib1g-dev libcap-ng-dev libcap-ng0 make libmagic-dev libjansson-dev libnss3-dev libgeoip-dev liblua5.1-dev libhiredis-dev libevent-dev python-yaml rustc cargo liblz4-dev -y- Install dependencies
cd /tmp && wget https://www.openinfosecfoundation.org/download/suricata-5.0.3.tar.gz- Download Suricata
tar -xvzf suricata-5.0.3.tar.gzcd /tmp/suricata-5.0.3LIBS="-lrt" ./configure --prefix=/usr --sysconfdir=/etc --localstatedir=/var --enable-pfring --with-libpfring-includes=/usr/local/include --with-libpfring-libraries=/usr/local/lib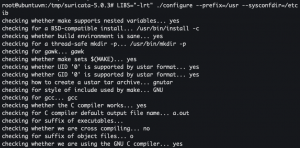
makemake installmake install-conf- Creates a log directory (/var/log/suricata), config directory (/etc/suricata), and a rules directory (/var/lib/suricata)
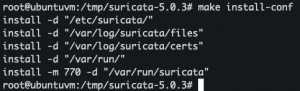
- Creates a log directory (/var/log/suricata), config directory (/etc/suricata), and a rules directory (/var/lib/suricata)
- Suricata.yaml
cp /etc/suricata/suricata.yaml /etc/suricata/suricata.yaml.bak- Create a backup of Suricata config
chmod 400 /etc/suricata/suricata.yaml.bakwget https://raw.githubusercontent.com/CptOfEvilMinions/BlogProjects/master/suricatav5-pf_ring/conf/suricata/suricata.yaml -O /etc/suricata/suricata.yaml- Download Suricata main config
sed -i 's/{{ monitoring_interface }}/<monitor interface>/g' /etc/suricata/suricata.yaml- Replace “{{ monitoring_interface }}” with the network interface you want to monitor
- Create a system user for Suricata
adduser --disabled-login --shell /bin/false --system --home /nonexistent --no-create-home --ingroup root suricatachown -R suricata:root /var/log/suricata
- Suricata defaults
wget https://raw.githubusercontent.com/CptOfEvilMinions/BlogProjects/master/suricatav5-pf_ring/conf/suricata/default_suricata_pf-ring -O /etc/default/suricata- Specifies the default settings to run Suricata
- Suricata service script
wget https://raw.githubusercontent.com/CptOfEvilMinions/BlogProjects/master/suricatav5-pf_ring/conf/suricata/suricata-pf_ring-init.sh -O /etc/init.d/suricatachmod +x /etc/init.d/suricata/etc/init.d/suricata start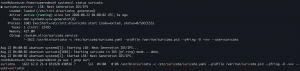
systemctl enable suricatasystemctl restart suricata
Setup Suricata-update for rules
mkdir /etc/suricata/rules- Make a directory for local rules
- Disable rules
touch /etc/suricata/rules/disable.conf- Place any rules you want to disable in this config
- Here for more information
- Custom rules
touch /etc/suricata/rules/local.rules- Place any custom rules you want in this config
wget https://raw.githubusercontent.com/CptOfEvilMinions/BlogProjects/master/suricatav5-pf_ring/conf/suricata/suricata_update.yaml -O /etc/suricata/update.yamlsed -i 's#{{ suricata_rules_dir }}#/etc/suricata/rules#g' /etc/suricata/update.yaml- Set the location of the Suricata custom rules directory
suricata-update- Init rules directory
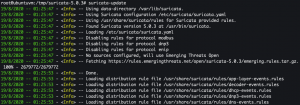
- Init rules directory
suricata-update update-sources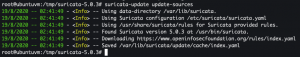
suricata-update list-sources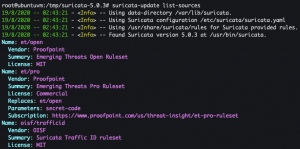
suricata-update enable-source <source>- Open source sources to enable
et/open– Emerging Threats Open Rulesetoisf/trafficid– Suricata Traffic ID rulesetptresearch/attackdetection– Positive Technologies Attack Detection Team rulesetsslbl/ssl-fp-blacklist– Abuse.ch SSL Blacklistsslbl/ja3-fingerprints– Abuse.ch Suricata JA3 Fingerprint Rulesetetnetera/aggressive– Etnetera aggressive IP blacklisttgreen/hunting– Threat hunting rules
- Open source sources to enable
suricata-updatesystemctl restart suricata
Testing Suricata
Ping test
echo 'alert icmp any any -> any any (msg:"PING detected"; sid:2; rev:1;)' >> /etc/suricata/rules/local.rulessuricata-update- We can see one new rule was added since the last update
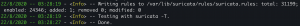
- We can see one new rule was added since the last update
systemctl restart suricataping -c 4 8.8.8.8cat /var/log/suricata/eve.json | grep 'event_type":"alert"'
Lessons learned
I am currently reading a book called “Cracking the Coding Interview” and it is a great book. One interesting part of the book is their matrix to describe projects you worked on and the matrix contains the following sections which are: challenges, mistakes/failures, enjoyed, leadership, conflicts, and what would you do differently. I am going to try and use this model at the end of my blog posts to summarize and reflect on the things I learn. I don’t blog to post things that I know, I blog to learn new things and to share the knowledge of my security research.
New skills/knowledge
- Compile Suricata v5.0.3 with pf_ring v7.6
- Suricata rule making
- How to configure suricata-update
- Learned how to use “{% raw %}” for Ansible templates
Challenges
- The default service init.d script doesn’t support PF_RING. I had to modify the original init.d script to include support for PF_RING.
- The only official guide to compile Suricata with PF_RING is from the Ubuntu 12.04 era.
- Ansible kept interpreting the
%din the Suricata.yaml config when it should have treated it as a string
What You’d Do Differently
- I wasn’t able to get PF_RING flow tables working to filter out traffic like Netflix and Youtube.
References
- Controlling which rules are used
- How to Install Kernel Headers in Ubuntu and Debian
- Github – ntop/PF_RING
- PF_RING FT (Flow Table)
- How to accelerate Bro with PF_RING FT
- Installation of Suricata stable with PF RING (STABLE) on Ubuntu server 12.04
- Detecting intruders with Suricata
- Suricata – Controlling which rules are used
- Suricata Update Documentation – Example Configuration File (/etc/suricata/update.yaml)
- Setting up the Suricata IDPS
- Bug#839146: suricata failures with systemd
- Github issuee – pf_ring init script doesn’t load drivers after rebuilding them upon kernel update
- How to Monitor Network Traffic with Virtualized Bro 2.51 on Ubuntu 16.04.2 on ESXi 6.5
- nDPI – Quick Start Guide
- Raw Packet Capture in the Cloud: PF_RING and Network Namespaces
- PART 1: INSTALL/SETUP ZEEK + PF_RING ON UBUNTU 18.04 ON PROXMOX 5.3 + OPENVSWITCH
Did you do this over the native Netplan networking service or did you replace Netplan with Network-Tools prior to configuration? Netplan does not support promiscuous interfaces at this time I believe.
Did you test packet capture?
Hey Frank,
Thanks for reading the blog and the feedback. Since this setup utilizes PF_RING it doesn’t rely on netplan. Therefore enabling promiscuous mode for Suricata is not a problem. Hope this helps 🙂
Hi Ben. Enjoying your blog. I have a question regarding Suricata on Ubuntu 20.x please. 20.x uses Netplan for it’s networking engine and Netplan doesn’t support promiscuous mode. Did this become an apparent problem as you configured it, and if so, how did you deal with it?
It would have been great to have seen your interface configurations, it’s not clear whether you use a single nic or more than one. Typically we want this type of device to have a dedicated management interface and a second interface for sniffing. Looking forward to your feedback.