Veracrypt provides on-the-fly encryption and is also the predecessor and a fork of the Truecrypt project. Back in Fall of 2015 the Truecrypt maintainer’s stated the code was “not secure”. When this happened it left the security community in a huge loss and swirl of what “not secure” meant. However, after several months the internet rolled on and someone decided to pickup the torch and keep running. In this guide I am just running through the installation of Veracrypt, creating Veracrypt containers, and creating hidden Veracrypt cotnainers on Mac OSX El Captain.
Install/Setup Veracrypt
- Download OSXFuse which is required by Veracrypt.
- Additionally, OSXFuse is a nice bonus because now you can write to NTFS partitions :).
- Instal OSXfuse
- Download Veracrypt
- Install Veracrypt
- Now once Veracrypt is installed we have access to mount or create Veracrypt containers.
Creating Veracrypt Container
- Open Veracrypt
- Select “Create volume”
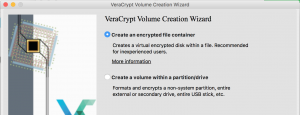
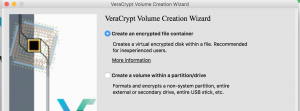
- This menu allows you to select the type of container.
- Encrypted File Container -A VeraCrypt volume can reside in a file, which is also called container, in a partition or drive.
- We are going to select “File Container” for this guide.
- Encrypted Partition/Drive Container – This option allows the user to encrypt a partition/drive where an operating system may reside.
- Please beware that Veracrypt supports full disk encryption for Windows and Linux.
- It is recommended to use LUKS on Linux systems.
- It is recommended to use LUKS on Linux systems.
- Please beware that Veracrypt supports full disk encryption for Windows and Linux.
- Encrypted File Container -A VeraCrypt volume can reside in a file, which is also called container, in a partition or drive.
- This page allows you to select the type of volume.
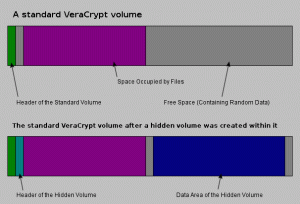
- Veracrypt Container Basics
- In the next few steps you will be choosing a static size for the Veracrypt container. Once a container is created it’s size cannot be changed unless you create a new container. The encryption process will take the entire space and encrypt it. This ensures that no one can read the file contents or guess the contents of the container based on the used space. To the attacker it’s just nothing but random bits.
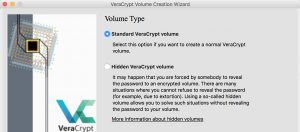
- Volume Type
- Standard VeraCrypt Volume – As seen above a standard container can contain files and free space. However to an adversary the container is all random bits so they can’t tell the contents of the container.
- We are going to select “Standard Veracrypt Volume”
- Hidden Veracrypt Volume – Since we know the entire container is encrypted we know it is impossible to detect a hidden volume. A hidden container works by putting a container inside a container. The Veracrypt container will have two passwords the first one is for the outer/fake portition and the second password if for the hidden portion.
- Standard VeraCrypt Volume – As seen above a standard container can contain files and free space. However to an adversary the container is all random bits so they can’t tell the contents of the container.
- This page allows you to create a file for the Veracrypt container OR insert the container to an existing file.
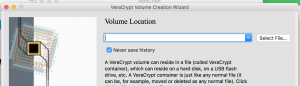
- For this guide we are going to create a new file.
- Select “Select file”
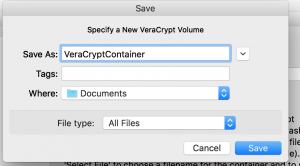
- Enter a name into Save As
- Enter a location to save the file for “Where”
- Select “Save”
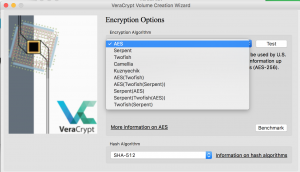
- This page allows you to choose the encryption algorithm and hash algorithm
- Encryption algorithm – Veracrypt gives the user the ability to select their preferred encryption algorithm. Please keep in mind once the encryption algorithm is chosen it can not be changed. Additionally, Veracrypt supports cascading encryption types for multiple layers of encryption.
- Hash algorithm – Veracrypt allows the use to select their preferred hashing algorithm. The hashing algorithm is used by the random number generator to create master/secondary keys and the salt.
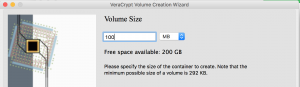
- This page allows you to determine the size of the Veracrypt container. Please keep in mind the container size and fixed and CANNOT be resized later.
- This page allows you to setup a password for the container, a keyfile for the container, and the PIM interation for the container
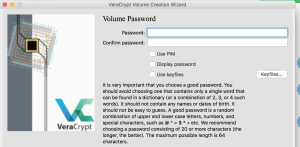
- Password – A string of alphanumeric characters used to unlock the container.
- Keyfile – A file whose contents should be unique and is combined with a password to unlock the container.
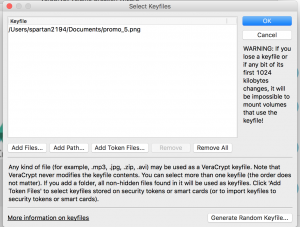
- PIM – A value that controls the number of iterations used by the header key derivation function. The PIM can be treated as a secret value that must be entered manually by the user everytime they want to unlock the container.
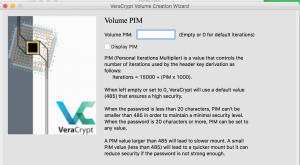
- This page allows you to choose the filesystem format. Depending on the operating system mounting this image this can be important. Additionally keep in mind the limitations of filesystems say for example FAT can support files up to 4GB.
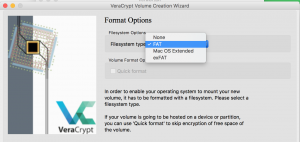
- This page is my favorite part. Veracrypt needs to generate a random pool of data for the key. They have this nifty tool that tracks your mouse movements and those random movements create entropy. So have fun and go nuts with your mouse!
- Select Format
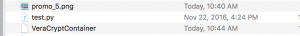
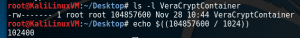
A fun lil tid bit about Veracrypt containers. So the internet will lead you to believe there are ways to detect Truecrypt containers however those methods are not perfect, nor do they have good accuracy(as of the date for this post). As you can see below when we run the file command on the container it just returns “DATA”. The best method to current date is all Veracrypt/Truecrypt containers are ALWAYS evenly divisible by 1024.
![]()
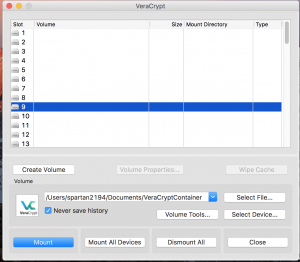
Mounting Veracrypt Container
- Open Veracrypt, select an open drive slot, and select “Select File”
- Find Veracrypt container and select open
- Once the file is loaded select “Mount”
- Enter password for Veracrypt container
- If your Veracrypt container needs a keyfile select “Keyfiles”
- Select “Add files”
- Find your file(s) and select “Ok”
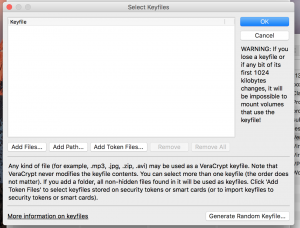
- Select “Mount”
- If you get error 255 for OSXFuse on Mac OSX
- brew install Caskroom/cask/osxfuse
- reboot
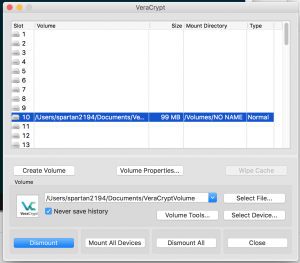
- To dismount select “Dismount”
Create a hidden container
- Open Veracrypt
- Select “Create volume”

- This menu allows you to select the type of container.
- Select “Encryted File Container” for container type
- Select “Hidden VeraCrypt Volume” for Volume Type
- his page allows you to create a file for the Veracrypt container OR insert the container to an existing file.

- For this guide we are going to create a new file.
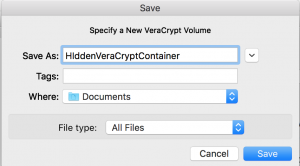
- Select “Select file”
- Enter a name into Save As
- Enter a location to save the file for “Where”
- Select “Save”
- This page allows you to choose the encryption algorithm and hash algorithm
- This page allows you to determine the size of the Veracrypt container. Please keep in mind the container size and fixed and CANNOT be resized later.
- Keep in mind the outside container must be big enough to contain the hidden container.

- Keep in mind the outside container must be big enough to contain the hidden container.
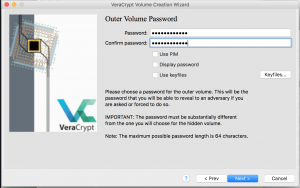
- This page allows you to setup a password for the OUTSIDE container, a keyfile for the container, and the PIM interation for the container.
- On the next screen move the mouse around to generate randomness and then select “Format”.
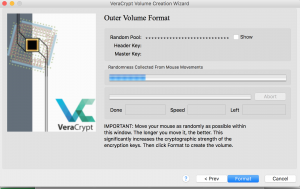
- Once the outside container is created you will be prompted with the following. From here we can open up the outer container and enter some data that looks like the treasurer :).
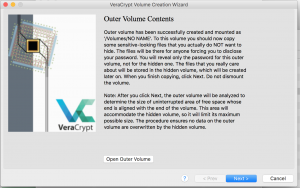
- The next page will allows to select encryption algorithm and hash algorithm.
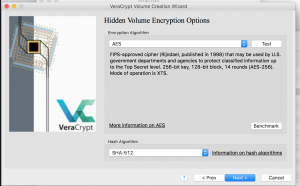
- This page allows you to enter the size of the hidden container. Keep in mind the hidden container can’t exceed the size of the outside container.
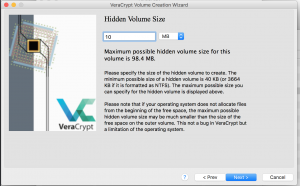
- This page allows you to enter a password for the hidden volume.
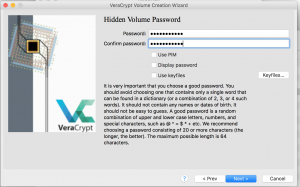
- Select filesystem type for a hidden Veracrypt container.
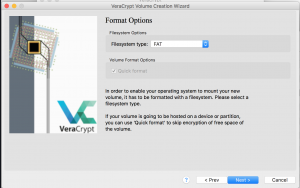
- On the next screen move the mouse around to generate randomness and then select “Format”.
- After the creation of the hidden container you will be prompted with the following:
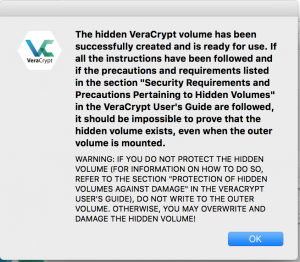
Mounting a hidden container
Open the outer container(Fake container)
- Open Veracrypt, select an open drive slot, and select “Select File”
- Find Veracrypt container and select open
- Once the file is loaded select “Mount”

- Enter password for the outer Veracrypt container.
- This will mount the container as a virtual drive. The driver can be used to retrieve and add files just like a normal container.
Open the hidden container
- Open Veracrypt, select an open drive slot, and select “Select File”
- Find Veracrypt container and select open
- Once the file is loaded select “Mount”

- Enter password for the hidden Veracrypt container
- This will mount the container as a virtual drive. The driver can be used to retrieve and add files just like a normal container.
- This container is also the hidden porition and allows the user to retrieve the hidden contents and add new files.
Resources/Sources